Microsoft announces six different versions of Windows 10
 Saturday, May 16, 2015 at 10:00AM
Saturday, May 16, 2015 at 10:00AM There will be six versions released, with Windows 10 Home, Windows 10 Mobile, Windows 10 Mobile Enterprise, Windows 10 Pro, Windows 10 Enterprise, and Windows 10 Education. As you can see, most people will opt for Home or Professional. Here is a quick run down from Mary Jo Foley:
Windows 10 Home: The consumer-focused desktop edition. This will include the core Windows 10 features, such as the Edge browser, Continuum tablet-mode for touch-capable devices; Cortana integration; free Photos, Maps, Mail, Calendar; Music and Video apps; and Windows Hello face-recognition/iris/fingerprint log-in for devices that support those technologies. On devices with screen sizes of 10.1 inches or less, users also will get Universal Office apps for free, once they are available.
Windows 10 Mobile: This is the SKU for Windows Phones and small Intel- and ARM-based tablets. ("Small" means between three and 7.99 inches in size.) This SKU will include the core Windows 10 features; free Universal Office apps once they are available; and support for Continuum for Phone, allowing customers to use phones as PCs connected to larger screens (but only on new devices supporting certain screen resolutions).
Windows 10 Mobile Enterprise: This is a version of Windows 10 Mobile for volume licensing customers only. According to the blog post, this SKU incorporates the latest security and feature updates to Windows 10 once they are available. There's no word if users will be able to delay these updates in order to test/stagger their delivery, which is offered under Windows Update for Business.
Windows 10 Pro: A desktop version of Windows 10 for mobile workers, tech enthusiasts and other power users. This version is one of at least two -- the other being Windows 10 Enterprise -- that will allow users to opt for Windows Update for Business. Windows Update for Business will allow admins to opt to not receive all feature and security updates from Microsoft immediately after they are available.
Windows 10 Enterprise: This is the Enterprise version of Windows 10 that is available to volume-licensing customers. This version is not part of Microsoft's first-year-free upgrade offer, but those with volume-licensing Software Assurance customers will be able to move to this version as part of their licensing terms. The Enterprise version customers get access to the Long Term Servicing Branch of Windows 10 -- which allows them to opt to receive security fixes only and no new features as Microsoft rolls them out.
Windows 10 Education: This is the version for staff, administrators, students and teachers, and will be available through academic Volume Licensing. Microsoft officials say there will be paths for schools and students to upgrade from Windows 10 Home and Pro, but don't yet provide details on that front.


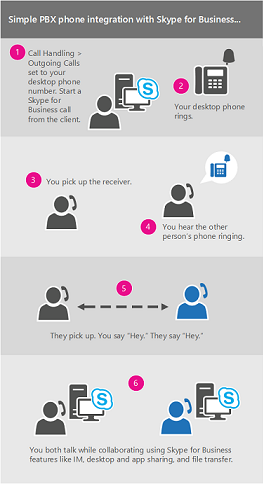
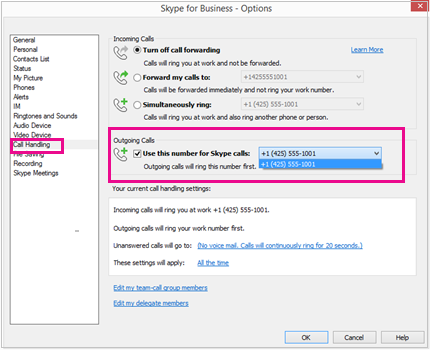



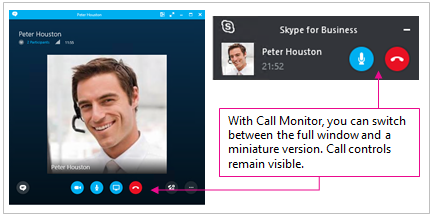


 Mobile devices and apps are pushing Wi-Fi to the limit and there’s no end in sight. Workers are determined to use enterprise apps on personally-owned devices to get more done and it’s placing a huge burden on corporate Wi-Fi networks. That’s why enterprise IT is migrating to 802.11ac, the gigabit Wi-Fi standard.
Mobile devices and apps are pushing Wi-Fi to the limit and there’s no end in sight. Workers are determined to use enterprise apps on personally-owned devices to get more done and it’s placing a huge burden on corporate Wi-Fi networks. That’s why enterprise IT is migrating to 802.11ac, the gigabit Wi-Fi standard. Laptop megabrand Lenovo was all over the news recently thanks to a preinstalled utility called
Laptop megabrand Lenovo was all over the news recently thanks to a preinstalled utility called


