PAConnect, Sophos and Cowbell: A Strategic Partnership for Cybersecurity
 Friday, April 7, 2023 at 7:03AM
Friday, April 7, 2023 at 7:03AM  Cybersecurity is one of the most pressing challenges for businesses in the digital age. As cyber threats become more sophisticated and frequent, organizations need to protect their data, systems and reputation from potential breaches and attacks. However, cybersecurity is not a one-size-fits-all solution. Different businesses have different needs, risks and budgets when it comes to securing their digital assets.
Cybersecurity is one of the most pressing challenges for businesses in the digital age. As cyber threats become more sophisticated and frequent, organizations need to protect their data, systems and reputation from potential breaches and attacks. However, cybersecurity is not a one-size-fits-all solution. Different businesses have different needs, risks and budgets when it comes to securing their digital assets.
That's why PAConnect, a leading IT solutions provider, has partnered with Sophos and Cowbell, two of the most innovative and trusted names in the cybersecurity industry. Together, they offer a comprehensive and customized cybersecurity package that combines cutting-edge technology, expert services and tailored insurance coverage.
Sophos is a global leader in next-generation cybersecurity solutions that protect millions of users across 150 countries. Sophos offers a range of products and services that cover endpoint protection, network security, cloud security, mobile security and more. Sophos also provides 24/7 threat intelligence and response through its SophosLabs and Sophos Managed Threat Response teams.
Cowbell is a cyber insurance company that leverages artificial intelligence and data science to assess and mitigate cyber risks. Cowbell offers cyber insurance policies that are tailored to each business's unique risk profile and exposure. Cowbell also provides proactive risk management tools and resources to help businesses improve their cybersecurity posture and resilience.
By partnering with Sophos and Cowbell, PAConnect can offer its clients a holistic and integrated approach to cybersecurity that covers prevention, detection, response and recovery. PAConnect can help its clients select the best Sophos products and services for their specific needs and budget, as well as provide installation, configuration, maintenance and support. PAConnect can also help its clients obtain the optimal Cowbell cyber insurance policy that covers their potential losses in case of a cyber incident.
With this strategic partnership, PAConnect, Sophos and Cowbell aim to provide businesses with the peace of mind that they are protected from cyber threats at all levels. Whether it's a ransomware attack, a data breach, a phishing scam or any other cyber risk, PAConnect, Sophos and Cowbell have the solutions to help businesses stay secure and resilient.
 Cowbell,
Cowbell,  Cyber Security,
Cyber Security,  Security,
Security,  Sophos
Sophos 



 Microsoft has been warning users about tech support scams for years, and this week shared how it is seeing these scams continue to evolve by
Microsoft has been warning users about tech support scams for years, and this week shared how it is seeing these scams continue to evolve by  By Bill Brenner,
By Bill Brenner, 
 As with the recent WannaCry Ransomware attack, organizations around the world have again been affected by a new ransomware variant known as the Petya cyber-attack. We wanted to contact you to offer our advice and support.
As with the recent WannaCry Ransomware attack, organizations around the world have again been affected by a new ransomware variant known as the Petya cyber-attack. We wanted to contact you to offer our advice and support. 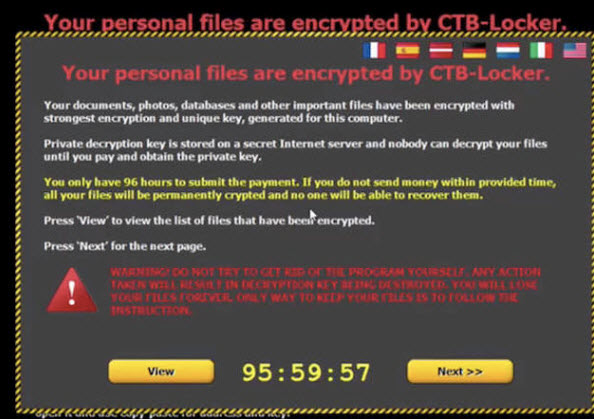
 Malware that encrypts all of a victim's files and holds them for ransom - what's commonly called crypto-ransomware or cryptoware - continues to be hugely successful in making money for the criminal gangs who perpetuate it.
Malware that encrypts all of a victim's files and holds them for ransom - what's commonly called crypto-ransomware or cryptoware - continues to be hugely successful in making money for the criminal gangs who perpetuate it.
 Cyber Security Awareness Contest for Students!
Cyber Security Awareness Contest for Students!
